A Pragmatic and Theoretical Approach.
![]()
![]()
![]()
![]()
![]() Terrorism and the United States:
Terrorism and the United States:
A Pragmatic and Theoretical Approach.
The events of September 11, 2001 were to say the very least, tragic. Although the horrendous acts that occurred in New York and Washington, DC can never be justified one must see the silver lining in the cloud. Thanks to a bombardment of information on the subject of terrorism by the mass media the American public has been awakened to the mysterious underworld of the terrorist. However, the common misconception brought about by this newly acquired information is that terrorists are small, clandestine groups of evil men who wish nothing more than to inflict pain and suffering on unsuspecting victims, namely civilians. This perception fits well into commonly used definitions of terrorism. One of many similar explanations characterizes terrorism as ��premeditated, politically motivated violence perpetrated against noncombatant targets by sub-national groups or clandestine agents, usually intended to influence an audience� (22.U.S.C. 2656 f(d)). Although this cookie cutter description may be fine for the ordinary citizen, it hardly covers all aspects of terrorism. It leaves out religious and economic motives for terrorism, for instance, but more importantly it does not define a well-known subject of terrorism: state terrorism. The US State Department tackles the issue though. They define a terrorist nation as one who engages in activities such as:
��the gathering of information in potential targets of terrorist activity,� and � the providing of any type of material support, including a safe house, transportation, communication, funds, false identification, weapons, explosives, or training, to any individual the actor knows or has reason to believe has committed or plans to commit a terrorist activity� (Immigration and Nationality Act, 1952).
This is implicitly the definition for state-sponsored terrorism rather than state terrorism. In the former the state does not directly participate in the acts themselves, although they help facilitate the action. In the latter (state terrorism) governments commit acts of terrorism on their own citizens with the use of government resources, such as the police or military (Atkins 1992; Henderson 2001; Liston 1977).
Upon reading the definitions given so far one could summarily place appropriate terrorist groups into the suitable definition. For instance, in the first definition given one could easily pronounce the group Shining Path, a communist and revolutionary group in Peru, as a terrorist organization. One could also label Libya and Iraq as sponsors of terrorism or terrorist-states. However, few would think to put traditional terrorist organizations (i.e. Shining Path) into the same group as state terrorists (i.e. Libya). Similarly few would put the government of the United States into either grouping. This paper will go against the grain and challenge traditional terrorism research and commit to a definition that is universal in how we define what is a terrorist. In this paper it is hypothesized that the United States government is a complex terrorist network.
This essay attempts to justify this hypothesis in two parts. First terrorism will be clearly defined. This definition will then be applied to select actions performed by the United States government in order to show that those activities are undeniably acts of terrorism. Secondly, a terrorist network typology created out of the research gathered for this paper outlines the organizational and functional structures needed to sustain terrorist networks (and subsequently those constructions of the United States government). Furthermore, since it is customary to apply acronyms to terrorist groups out of convenience (e.g. Red Army Faction (RAF)), the United States government will often be referred to as USG.
There have been dozens in academia who have attempted to precisely define terrorism. It is not a term limited to a few lines; rather an entire book could be dedicated to its definition. Certainly many distinctions need to be made, such as the difference between terrorism and state-terrorism, guerilla warfare and terrorism, criminal acts and terrorism, and so on. David Whittaker (The Terrorism Reader, 2001) has put forth a definition that, above all others, seems to be the most sound in defining terrorism. According to Whittaker, terrorism and terrorists are:
1. Ineluctably political in aims and motives.
2. Violent � or equally important, threatens violence.
3. Designed to have far-reaching psychological repercussions beyond the immediate victim or target.
4. Conducted by an organization with an identifiable chain of command or conspiratorial cell structure (whose members wear no uniform or identifying insignia)�.
Whittaker also gives a fifth element to his definition that includes the words �subnational group or non-state entity� in which one can take issue with. The purpose of this paper, however, is to show that there is no difference between the terrorism caused by a state or a non-state group. A part of Stephen Atkins� definition could also be added to Whittaker�s, however his notion that �A state consents to terrorists finding sanctuary before and after performing acts of terrorism� (Terrorism: A Reference Handbook, 1992) could be redundant, because a state who performs acts of terrorism will obviously find sanctuary within its own borders.
1. Ineluctably political in aims and motives � What greater reason is there for the United States to get involved in suspect activities than for political reasons? Politics is the game played by governments and powerful people around the world, and the USG is a formidable player in this game. Fundamentally all of its foreign policy is done for political reasons. Author Charles W. Kegley (American Foreign Policy: Pattern and Process, 1991) notes that there is a ��striking consistency in the willingness of postwar administrations to intervene in the affairs of others� (86). This intervention is necessary to carry out USG political agendas. One issue the USG has constantly made itself a participant of is that of Fidel Castro and Cuba. From the start the USG has not approved of Castro�s socialist and dictatorial role as the leader of Cuba, a tiny island nation that sits a mere ninety miles off USG territory. The politics of the USG dictated its agenda towards Cuba and consequently bore an unfriendly diplomatic relationship. �Concerning Cuba, the policy of the ultra-right and powerful forces in the Pentagon was at the time for an outright, full scale invasion and an attempt at re-enslavement of Cuba� (Hall Imperialism Today, 1972). With its various theories on the threats of communism and other non-democratic forms of government it was imperative to the USG�s agenda that it be involved in the ousting of Fidel Castro. It was largely seen that if one communist nation were to exist, then neighboring countries would soon follow in that ideological direction. This was a product of the Domino Theory and something that the USG would not allow.
Other nearby nations were subject to the terrorism of USG foreign policy. Manuel Noriega, former leader of Panama, was subject to such political directives. In 1982 the US Congress denied funds to Panama and it was well known that American interests in Panama were essentially that of �friendly control of the Panama Canal� (Kegley 1991; 407, 557). Indeed friendly control of the Panama Canal was necessary for the USG in order to maintain not only political control over the region but for strategic military purposes as well. In 1989 the USG sent an invasion force of 24,000 soldiers to Panama, even though there was no communist threat perceived (88). �Not only that, Grenada in 1982, Lebanon in 1982, Libya in 1986, Haiti in 1990 and Guatemala in 1982 were invaded by the American troops all in the name of not being satisfied with the then political climate of these countries� (Kagara 2001).
The Cold War was a political chess game played between the two great superpowers � the USG and USSR. Many nations and leaders throughout the globe felt the presence and pressure of the USG as it struggled to maintain political supremacy. �It [America] has footprints of dirty and supercilious diplomacy characterized by oppression, suppression and repression with a lingua franca of violence� (Kagara 2001). All too often the USG uses its diplomatic muscle to gain �friendly� political relationships around the globe.
2. Violent � or equally important, threatens violence � The USG is notorious for using violent means to achieve its ends. In fact the use of its military may be the most effective way it can assure success in a given conflict. Probably the most gratuitous use of violence by this network was the use of the atomic bomb in 1945 on Japan. Thousands of innocent civilians were murdered by the use of this weapon and no remorse was shown by the USG. In his memoirs President Harry Truman said he ��regarded the bomb as a military weapon and never had any doubt that it should be used� (Truman 1995; 49). The Franck Committee on a Non-Combat Atomic Demonstration (1945), an independent scientific committee, pleaded with the USG not to use the weapon against civilians and instead advocated a demonstration in front of representatives from every nation (including Japan). The committee implicitly denounced the secret use of the atomic bomb (Paterson 1984; 286). This was to no avail.
Another infamous occurrence of the use of extraordinary violence by the USG was in the tiny village of My Lai, Vietnam. There 504 innocent men, women, children, babies and senior citizens were summarily executed by USG soldiers (Anderson 1998; 2-4). Under the suspicion that the village was harboring a mass of weapons, commanding officer Lt. William Calley gave the orders to massacre the village people and even participated in the murders. Later only three weapons were found in the village. Calley was only later accused of murdering �at least 22� noncombatants (204-5). Even today the USG is using excessive violence to seek revenge for the attacks of September 11, 2001. Whereas on that historic day approximately 3200 innocent Americans were killed (National Review December 17, 2001), to date in Afghanistan between 3000 and 8000 innocent Afghans have been killed by USG military machinery (The Guardian via Refuse and Resist February 12, 2002). There is no doubt that the USG uses violence as a means to achieve its ends.
3. Designed to have far-reaching psychological repercussions beyond the immediate victim or target � Acts of terrorism not only affect the immediate target but they affect the public emotionally and psychologically as well. The USG has been known to employ such tactics in the past to get what it wants. In its early history such strategies were used on the Native American population of what is now the Continental United States. Thomas Jefferson, third president of the United States committed the USG to the �removal of the Indians� (Zinn 1995; 125). Under the guise of Manifest Destiny the USG set itself on a course to eradicate the land of �savages.� Coined by John L. O�Sullivan the term Manifest Destiny became an instant battle cry for American expansion to the Pacific Ocean in the mid-1850s. In an editorial written for the New York Morning News O�Sullivan greatly advocated westward expansion and referred to the Spanish-Indian-American populations as a �mixed and confused blood� (Current 1965; 441), a sentiment that surely became bigoted justification for the eradication of those First Nations. The years 1838 and 1839, the period commonly referred to as the Trail of Tears, saw the worst of this mentality as there were multiple forced migrations of the indigenous populations. Every single peace or land treaty between the USG and the Native American populations was broken by the USG (Zinn 1995). These tactics were designed to have psychological impacts on the rest of the indigenous tribes.
The USG consistently played mind games with the Cuban leadership and Cuban public throughout the Cold War as well. �The so-called assurances given by the United States that it will not invade Cuba are nothing but a hoax. �In fact the danger of invasion is even greater. �The invasion is imminent� (Peking Review, Hall 1972; 205). This statement was on target as the Bay of Pigs invasion later took place. Additionally the Interior Committee on Military Use of the Atomic Bomb (1945) advocated using the bomb in Japan for military as well as for psychological purposes. Their stated goal was to ��seek a profound psychological impression on as many of the inhabitants as possible� (Paterson 1984; 285). Constant bombing in Vietnam, Laos and Cambodia during the Vietnam War was also designed to have psychological repercussions on the Vietnamese population (Sheehan 1971; 504). Even today detentions of Afghans and suspected �terrorists� are jailed without due process in order to �send a message� to other extremists. To put it simply: Terrorists use tactics that are designed to affect a large population psychologically so that it [the public] will concede to their demands.
4. Conducted by an organization with an identifiable chain of command or conspiratorial cell structure (whose members wear no uniform or identifying insignia) � There is no doubt that the USG has an identifiable chain of command as well as a conspiratorial cell structure. The president sits at the top of the military, hierarchical pyramid (as Commander-in-Chief) and the chain continues down to the bottom where the common soldiers are slotted. The clandestine operations of the Central Intelligence Agency (CIA) and the National Security Agency (NSA) also fit well into this component of the definition. The USG, through its CIA channel, put into power Manuel Noriega in Panama in part as a �new crusade on behalf of democracy� (Kegley 1991; 110). Additionally the CIA was involved in many assassination attempts of Cuban leader Fidel Castro. These attempts included ��High powered rifles to poisoned pens, deadly bacterial powders, and other devices�� There were even plans to give Castro drugs that gave him LSD like effects and powders that would make his beard fall out, (Paterson 1984; 527-8). The CIA has a huge budget ($26.7 billion in 1998) and the NSA�s budget is for the most part unknown (www.fas.org/sgp/foia/intel98.html, April 28, 2002). With these resources secret missions on behalf of the USG not only vary in purpose but they are plentiful too. In his paper The CIA Under Clinton: Continuity and Change, Christopher Jones reports that ��The CIA develops and operates state-of-the-art technical collection instruments; conducts covert political and paramilitary operations; engages in counterintelligence activities (e.g. counterespionage and security efforts)� (2001: 506) The CIA, an organ of the USG, has certainly had its hands in a number of secret and suspect missions around the world. By acting under cover and by its members not identifying itself as part of such a group, the USG has certainly involved itself in terrorist activities.
Through these few but various examples of USG foreign and domestic policy, and engagements it is easy to see how the United States government could easily fall into Whittaker�s definition of terrorism. Be it a use of political tactics, military force, psychological mechanisms, or clandestine operations, the USG has clearly undertaken terrorist activities and thus must be considered a terrorist organization. The physical limitations of this paper hinder the amount of relevant information on USG activities that can be applied to the definition. Certainly there is enough subject matter to fill volumes. However, if one is still not convinced that defining such measures is not justification enough for labeling the USG a terrorist network, a typology may be used to further the claim that it is such.
Research accumulated for this paper indicates that terrorist organizations need to sustain a certain organizational and functional structure in order to be deemed a terrorist network. In other words, they need certain mechanisms of function and structure to keep them from failing. If organizations accused of being �terrorist� did not fit such a model then it could be that they fall into an entirely alternative definition (such as guerilla group, criminal gang, etc.). Perhaps the given examples do not need all the facets of this typology in order to survive and therefore they may function by different modes. Admittedly further research into the subject is required.
The model in Table 2 was constructed in an attempt to explain terrorist networks. It examines the various components that a terrorist organization needs to maintain in order to be deemed �terrorist.� The genesis for such a construct was inspired by the Executive Director of the International Policy Institute for Counter-Terrorism, Boaz Ganor, who suggested that a pyramidal, hierarchical structure would best define a [state sponsored] terrorist organization (Countering State-Sponsored Terrorism, 1998). However his design (Table 1) was missing elements that are vital for a terrorist organization�s success, such as intelligence gathering, propaganda distribution, and perhaps the use of coercion. Additionally Ganor�s use of a pyramid suggests that all of his elements need to function in a systematic fashion (ideology to implementation) in order for a terrorist operation to be enacted.
Table 1
|
I |
II |
|
|
|
|
Ganor, Boaz. Countering State-Sponsored Terrorism. The International Policy Institute For Counter-Terrorism. April 25, 1998. |
|
With this new model it is posited that not all operations are needed for a terrorist act to be implemented, but instead only some or most of the aspects need to be employed, and not necessarily in any specific order. No element of the organizational/functional model is critical for another to be initiated and so they are all on an equal plane. For example: A terrorist group does not necessarily need publicity in order to carry out a specific activity. Nevertheless, from a long-term perspective it does need publicity and propaganda in order to boost its ideological support and to increase visibility. To use another example: A terrorist network does not need operational elements to execute every terrorist action. Instead they may use coercion (such as bribery or sanctions). However operational forces are necessary in order to maintain the terrorist network�s agenda over a long period. Operational and military tactics are necessary to achieve the organization�s ultimate goals. Remember that terrorists are defined as inevitably violent. In other words, although it is unnecessary for all elements to be enacted on any given terrorist action, activation of all elements over an extended time period is necessary for the terrorist group to survive long-term.
The model asserts that there are seven variables that make up a terrorist organizational and functional structure: Leader, Intelligence, Finances, Operational, Ideology, Publicity/Propaganda, and Clandestine Groups/Members. An eighth variable, Coercion is listed with a question mark because the relevance of that element to a terrorist organization is at best, questionable. Notice that examples of each element are given next to the USG variable. This is just a sampling of the means in which each facet is carried through and by no means is it an exhaustive list. Additionally one will notice the abbreviation AQ. This acronym represents the traditional terrorist group Al-Qaeda, a topical and well-known organization. The reason for the inclusion of Al Qaeda in the terrorist typology is to show the reader that this construct can be applied universally.
![]()




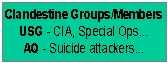

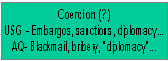
It is hoped that one can substitute any terrorist organization into this chart, be it a traditional terrorist network or a suspected state-terrorist nation. As mentioned earlier, this paper asserts that all terrorist networks can be inserted into the same typology. This construct complements Jessica Stern�s definition of terrorism, which avoids ��limiting perpetrator or purpose,� and ��Allows for a range of possible actors (states or their surrogates, international groups, or a single individual) for all putative goals (political, religious, or economic) and for murder for its own sake� (The Ultimate Terrorists 1999; 11). For consistency and parallelism Al Qaeda was used throughout the chart, and to keep with the theme that the United States government is a terrorist network, it too was inserted into the construct. Thus, further elaboration on the original hypothesis is warranted.
Leader � This is the most straightforward aspect of the typology. A terrorist network needs a leader to move the group in a given direction. Without a leader the group has no direction and cannot properly function. Often he has the ultimate say in every aspect of the organizations policy and actions. For the USG the leader is the President.
Finances � Terrorism is not free. Sometimes it is very expensive and other times it is very cheap, but it is never free. A source of income is needed in order for the organization to implement its activities. Traditional terrorist groups achieve this through robbery, ransom, blackmail, drug sales, and by various other devious methods. The USG gains its funds through taxation, both at the corporate level and citizen level. Although it receives most of its funds in this manner often the USG ��spends more than they are willing to tax from their citizens and so are forced to borrow� from international banks� (Allen None Dare Call it Conspiracy, 1972; 37-8). With 280 million plus citizens the USG has a plethora of such income - often achieving such ends through manipulative means. Author John McManus (Financial Terrorism, 1993) tells of various methods the USG practices in order to dupe an unsuspecting and naive public. �Experts at the federal level,� he says, �take funds they lead the public to believe are untouchable (funds for social security, highway building and maintenance, etc) and use them to pay other federal obligations� (90). Undoubtedly some of those �obligations� are acts that are terrorist by nature. McManus notes that such tactics of sleight of hand are not uncommon (89). Taxation and other methods of revenue accumulation are ingenious methods used by the USG to collect monies to fund its various legitimate and suspect activities.
Ideological Support � Often a terrorist group�s ideology comes from religious texts, sympathizers to the �cause,� etc. The USG ideology is that of its ruling political party. It is legitimized legally through elections. The winner-take-all system of the Electoral College is one that allows the elected leader to promote his ideological agenda both domestically and internationally. Other nations recognize the legitimacy of the elected leader and the American public as a whole accepts that the president�s ideology is their ideology. Nevertheless, the USG does not just maintain its ideological support from within; it gets it from without as well.
Through the exportation of its ideology on budding international leaders and governments the USG maintains its ideological supremacy throughout the world. One of the ways in which this is accomplished is through the Western Hemisphere Institute for Security Cooperation (WHISC), or as it was once known, the School of Americas. On the homepage of the independent organization School of Americas Watch one can find a brief description of what the WHISC does. It ��trains Latin American soldiers in combat, counter-insurgency, and counter-narcotics. Graduates of the SOA [WHISC] are responsible for some of the worst human rights abuses in Latin America.� Among some of its more notorious graduates are dictators Manuel Noriega and Omar Torrijos of Panama and some of its other 60,000 graduates ��have participated in human rights abuses that include the assassination of Archbishop Oscar Romero and the El Mozote Massacre of 900 civilians� (www.soaw.org).
The USG has also been known to set up �friendly� governments too. For example, critic Noam Chomsky tells that in 1948 the National Security Council ��secretly called for military support for underground operations in Italy along with national mobilization in the United States, �in the event the Communists obtain domination of the Italian government by legal means�� (Deterring Democracy, 1992; 345). Another example involves Vietnam. In a memo sent to Secretary Rusk it is deemed necessary (to the USG) that the Diem administration be overthrown because Diem�s ability to govern would not have gained the support of ��people who count� not to mention the American people� (Sheehan The Pentagon Papers 1971; 197). Another example: In referring to the Bay of Pigs invasion and other foreign policy initiatives towards Cuba Gus Hall, former General Secretary of the Communist Party USA, notes in Imperialism Today (1972) that �The aim of the policy was and remains the destruction of socialist Cuba� (202). Regimes that were not friendly with the USG were often the target of such tactics. Thus in order to retain ideological support from many nations the USG secretly attempts to and sometimes succeeds in establishing favorable governments.
Operational � Terrorist groups according to the earlier stated definition are �ineluctably violent.� Operational actions are the means to carry out such violence. The USG has vast resources that can carry out any number of operational activities. Whereas most terrorist groups have a handful of soldiers or at best a small army the USG has available an Army, Navy, Air Force, Marine Corps, Coast Guard, reserves and so on; not to mention the most technologically advanced weaponry in the world. The USG exploits such power and uses it to its full advantage. For instance, the USG used more than 500,000 combatants to crush an Iraqi invasion of Kuwait. Few organizations can match such power.
However this power has been used extensively for terrorist activities. One of the most remarkable examples of this abuse is USG intervention in Vietnam. Its military machinery was exuberantly exported to the tiny nation as one of many memorandums shows in Sheehan�s The Pentagon Papers (1971). In a memo sent after the recent Gulf of Tonkin �incident� William Bundy advocates the use of an extraordinary amount of might to achieve USG goals citing that �Negotiation� without continued military action will not achieve our objectives in the foreseeable future� pressure will continue until we have achieved our objectives� (295). Phases Two and Three of the same memo advocate �limited pressures� then �more serious pressures� respectively (296, 298). In November 1964 an advisory group to the leader of the USG gave three options in dealing with North Vietnam and all three options advocated bombing � none were diplomatic. The next month the USG commenced with Operation Barrel Roll, a secret and extensive air-strike campaign against the North and parts of Laos (308-9). The use of the atomic bomb, invasion forces of Central America, soldiers stationed around the world, and so on are a few more illustrations of many operational tactics the USG uses to further its ideology.
Intelligence � Intelligence is necessary for a terrorist organization to be effective and successful. In traditional terrorist groups intelligence officials may gather routine information such as a political candidate�s itinerary, the schedules of visiting influential and powerful diplomats, the acquisition of certain official documentation (i.e. passports) and so on. The USG too has a number of intelligence channels (FBI, NSA, etc), the most notorious being the Central Intelligence Agency (CIA).
The National Security Act of 1947 created the Office of Strategic Services (OSS). The CIA was an offspring of this branch. According to John Spanier (American Foreign Policy Since World War II, 1998) the OSS gathered foreign intelligence and conducted secret spy operations during World War II, but then was disbanded after the war. It was the CIA that stuck around and became an essential tool (53).
In keeping with the Vietnam example we can see the CIA being used in a variety of ways. A special team was a part of what was called the First Operation Group whose basic job was to make way for a future USG operational deployment. In or around July of 1961 the CIA was essential in gathering intelligence information and also partnered with the Vietnamese Intelligence Service and the covert Army Psychological Warfare Directorate (Sheehan, 132). Another meeting occurred in 1963 between General Duong Van Minh and a CIA operative where, among other things, the assassination of Ngo Dinh Nhu and Ngo Dinh Can of South Vietnam, were discussed. These operations and others of course paved the way for future USG operational activities in Vietnam.
The CIA is a vital organ of the USG and at virtually any cost it is necessary for the USG to maintain the CIA�s departmental abilities. One example of how far the USG will go to maintain intelligence supremacy occurred in Australia. ��There is evidence of CIA involvement in a virtual coup that overturned the Whitlam Labor government in Australia in 1975 when it was feared that Whitlam might interfere with Washington�s military and intelligence bases in Australia (Chomsky, 332). The USG realizes that, as a whole, without a thriving intelligence branch it will not be a successful organization. It would also be more susceptible to molestation from other terrorist organizations.
Publicity/Propaganda � These two elements are essential if a terrorist organization wants to be successful. Without propaganda funding would surely slow to a trickle and ideological support would wane. Without publicity their causes and stunts would be lost. Traditional terrorist groups utilize conventional methods of distributing their propaganda such as literature, video, word of mouth and more recently the World Wide Web. The USG is more sophisticated in how it distributes such information. It uses to its great advantage the mass (domestic and international) media.
It is well known that the more information the public has about a given conflict (especially military conflicts) the less likely it is to be supportive of military intervention (Frederking, Lecture: January 23, 2002). The less the public knows on a given subject the more latitude a leader has in forwarding his own agenda. Likewise the more popular a leader is the more leeway he has to do virtually what he wants (Kegley 1991; 301). The USG knows this and thus manipulates information distribution to the public via the mass media. In an interview with Clamor Magazine (January/February 2002) former Weather Underground member comments on this phenomenon:
We [the American public] are living isolated lives in our shattered communities, and in our names the US project shatters communities everywhere � in the Middle East, in Colombia, in the Philippines. The world roils in agony and despair, the catastrophe deepens, and our ears are covered, our eyes are closed.
The USG maintains its agenda by creative control of the publicity and propaganda it makes available to its supporters (the masses). In describing the three principles of his job former press secretary Mike McCurry maintains that he was supposed to tell the truth, give the public a window into the White House, and to protect the president (Kurtz Spin Cycle 1998; 15). Often the last duty gets in the way of performing the first two and more often than not the leader of the USG is protected first, and factual information is distributed second. According to author James Fallows the media often lets the politicians dictate what is news and not the other way around. Instead of investigating and actually digging up stories they allow leaders to determine what is and what is not an issue (Breaking the News�1997; 177). Walter Lippmann�s famous book Public Opinion (1922; 1997) details how the USG formulated a group of experts who would effectively manage the publicity directed to the American public by facilitating conclusions for the public to follow. This was done with the expectation that the public would be complacent with USG propaganda. It worked. The mass media is an effective tool the USG uses to govern publicity and propaganda aimed toward its citizenry and the rest of the world.
Clandestine � Once again the Central Intelligence Agency is lauded as the USG�s most significant channel for clandestine operations. Along with other factions, such as special operation units (e.g. Delta Force), the CIA conducts various secret operations around the globe.
One of many infamous missions initiated by the CIA was the Bay of Pigs invasion on Cuba. Gus Hall notes in his book Imperialism Today, the ��Pressures for an armed attack, for a massive bombing of Cuba came from many quarters� (1972; 203). The CIA responded and initiated one of its biggest debacles to date with the failed sponsorship of its invasion of Cuba by Castro dissident rebels. Trumbull Higgins (The Perfect Failure: Kennedy, Eisenhower and the CIA at the Bay of Pigs, 1989) reports, ��The only way Eisenhower had left to oppose communism by force was through the secret operations of the Central Intelligence Agency� (19). Often CIA operations were in direct contradiction of State Department policy and nearly ��3/4 of all covert-action projects would never be reviewed or approved by any committee outside the agency itself before action was undertaken� (37, 38).
The CIA and its dealings with Cuba are perhaps its most infamous, but Cuba was not its sole target. Clandestine operations as far as Italy and a movement to thwart legitimate democratic elections can be traced, as well as interference in Central America and the former Soviet Union (Chomsky 1992). The use of clandestine operations is one of the most effective ways for the USG to promote its ideological agenda.
Coercion � As mentioned before the coercion element is the most questionable aspect of the typology (Table 2). This is because so many policies and actions can be slotted into this facet. One definition for coercion is, �The application of sanctions or force by a government usually accompanied by the suppression of constitutional liberties in order to compel dissenters to conform� (Webster�s Third New International Dictionary 1968). For the purposes of this paper one should dismiss the term �government� from the definition because individuals and groups as well as governments can coerce.
The first part of the definition deals with economics: sanctions. Traditional terrorist groups may use blackmail or bribery to achieve their ends. In going with this theme, various methods of economic terrorism the USG has employed can be distinguished. With its overwhelming economic resources the USG can assert its agenda onto the rest of the world. The following excerpt from John Odell�s essay Explaining Change in Foreign Economic Policy demonstrates just how powerful the USG can be:
�States accounting for relatively small shares of world exports, imports, or credit have lesser means with which to reward or punish other states, and therefore their wishes are less likely to be complied with� (1996; 38-66).
The USG uses its economic might often to achieve its goals. Examples include economic sanctions on Iraq and Cuba, excessive deposits into the International Monetary Fund (IMF), and even by freezing financial assets of suspected terrorists and organizations. In one case involving Panama the USG dismissed diplomatic means and went straight to economic sanctions and military intervention (Kegley American Foreign Policy: Pattern and Process, 1991; 88).
The second part of the definition deals with the use of force and/or the suppression of civil liberties. The USG is no stranger to such tactics as even now prisoners at Guantanamo Bay, Cuba have been denied the rights of due process. The writ of habeas corpus was suspended during the American Civil War as well. Some scholars, such as John Spanier, believe that coercion was not always an effective tool for the USG though. He says, ��Great-power coercion was said to play a minimal role in resolving welfare issues, in strong contrast to primary roles it might play in secular issues.� Spanier goes on to say that frequent use of coercion would alienate (Third World) nations who export raw materials and have collective political clout (American Foreign Policy Since World War II, 1998; 191). Therefore coercion may not be a viable addition to the terrorist typology that has been set forth. Further research into this realm is required in order to make a solid determination, but that does not preclude the theoretical implications such an addition would have on a terrorist functional/organizational typology.
To conclude Part 2 it is important to note that the instances given to connect USG action to elements of the typology (Table 2) are select and are in no way exhaustive. Furthermore it is stressed that the typology employed here is an attempt at a universal model for terrorist structural function. The use of the United States government in this paper is two-fold. While this paper is slanted and is a poke at US policy, it is important to note that the US is just one of many governments accused of terrorist activities that can be plugged into the model. Additionally so-called traditional terrorist groups can be submitted to the same model and thus the implication is that there is no distinction between national and sub-national terrorist activity. A terrorist is a terrorist.
Conclusion - One may notice that most of the subject matter of this paper deals with USG foreign policy. This does not imply that domestic policies and actions cannot be submitted to the typology or to the definition: quite the contrary. Slavery, the concept of Manifest Destiny, shootings at Kent State and Jackson, as well as McCarthyism are just some examples of various forms of terrorism (by the given definition) that can be applied to the typology as well. One should not dismiss such USG undertakings; instead one should consider them, in one way or another, as acts of terrorism.
It was initially hypothesized that the United States government is a complex terrorist network. In Part 1 Whittaker�s definition that terrorists are political, violent, psychologically effective, and organized (and sometimes clandestine) (The Terrorism Reader 2001) was applied to some of the USG�s foreign and domestic activities. Ample evidence was given to sustain the hypothesis in this aspect. In Part 2 a universal typology (generated by research for this paper) was applied again to US foreign and domestic activities. It was also suggested that this model (Table 2) could be applied universally to all terrorist factions, however further research is needed to be conclusive on this last point. Thus, the application of the terrorist functional and organizational typology to the USG and its assertion that the USG is a terrorist network nets an inconclusive judgment. Although enough correlation between USG policy and action and terrorist network functionality was made, it cannot be proclaimed beyond a reasonable doubt that the USG is a terrorist network. In this aspect the typology does not necessarily sustain the hypothesis. This conclusion is based on the particulars that the typology does not consider. For instance, the USG is often charitable, democratic, law abiding (internationally) and more. One can claim that most traditional terrorist organizations lack such qualities. Furthermore, the USG is self-sufficient in generating resources, an internationally recognized governmental body, and for the most part, effective in its campaigns. Again, perhaps the same cannot be said about most traditional terrorist networks.
There are several philosophical implications of this paper. First, the hypothesis that the United States government is a terrorist network is sustained by the given definition. Therefore it is plausible that a universal definition of terrorism can be applied to all terrorist activities and groups. Nevertheless, the paper declared in the beginning that the hypothesis could be sustained by both the definition and the new terrorist organizational and functional typology. The latter did not sustain the hypothesis, though results are ultimately inconclusive. This too lends to the idea that there might be a universal terrorist typology that can be applied to all terrorist organizations. Further research in which multiple states and traditional terrorist networks are inserted into the typology is needed in order to make this determination.
The essence of this paper is not entirely a re-invention of the wheel. A number of dissidents of American foreign and domestic policy (e.g. Noam Chomsky, Howard Zinn, Michael Albert, etc) have labeled the United States government as terrorist. However, this paper has new theoretical implications in that it has attempted to create both a universal definition of terrorists/terrorism and a terrorist organizational and functional paradigm. If such models can be sustained then perhaps a universal method of counter-terrorism can be developed as well. Until then the subject of terrorism remains speculative.
References
Allen, Gary. 1972. None Dare Call it Conspiracy. Seal Beach, CA: Concord Press.
Anderson, David L. 1998. Facing My Lai: Moving Beyond the Massacre. Lawrence, KS:
Univ. Press of Kansas.
Atkins, Stephen E. 1992. Terrorism: A Reference Handbook. Santa Barbara: ABC-CLIO,
Inc.
Badey, Thomas. 1998. �Defining International Terrorism: A Pragmatic Approach.�
Terrorism and Political Violence. Spring: 90�107.
Chomsky, Noam. 1992. Deterring Democracy. New York: Hilland Wang.
Current, Richard N., and John A. Garraty. 1965. Words that Made American History:
Colonial Times to the 1870s. Boston: Little, Brown & Company.
Fallows, James. 1997. Breaking the News: How the Media Undermine American
Democracy. New York: Vintage Books.
Federation of American Scientists. 2002. �CIA Announces Disclosure of FY98
Intelligence Budget Total.� http://www.fas.org/sgp/foia/intel98.html. March 28.
Frederking, Brian. 2002. 9/11: An Act of War or Crime Against Humanity? Lecture.
January 23, McKendree College.
Ganor, Boaz. Countering State-Sponsored Terrorism. The International Policy Institute
For Counter-Terrorism. April 25, 1998.
Grove, Philip Babcock. Ed. 1968. Webster�s Third New International Dictionary.
Springfield, MA: G and C Meniam Co.
Guardian, The. 2002. �Afghans are still dying as air strikes go on. But no one is
counting.� Refuse & Resist. http://www.refusandresist.org/newwar/021202bombings.html. March 22.
Hall, Gus. 1972. Imperialism Today. New York: International Publishers.
Henderson, Harry. 2001. Terrorism. New York: Facts on File.
Higgins, Trumbull. 1989. The Perfect Failure: Kennedy, Eisenhower and the CIA at the
Bay of Pigs. New York: W.W. Norton & Co.
Immigration and Nationality Act, 1952.
Jones Jr., Alan M. 1973. US Foreign Policy in a Changing World. New York: David
McKay Company Inc.
Jones, Christopher M. 2001. �The CIA Under Clinton: Continuity and Change.�
International Journal of Intelligence and Counterintelligence. 14:503-28.
Kagara, Hussaini Sani. 2001. �Global Terrorism and its Therapy.� Africa News Service.
November 8.
Kegley Jr., Charles W., and Eugene Wittkopf. 1991. American Foreign Policy: Pattern
and Process. New York: St. Martin�s Press.
Kurtz, Howard. 1998. Spin Cycle. New York: Touchstone.
Lippman, Walter. 1997. Public Opinion. New York: Free Press.
Liston, Robert A. 1977. Terrorism. Nashville: Thomas Nelson Inc. Publishers.
Martin, Eamon. 2002. �The United States of Amnesia: Discussing Dissent and Terrorism
with Former Weather Underground Member Bill Ayers.� Clamor Magazine.
January/February: 20-24.
McManus, John F. 1993. Financial Terrorism: Hijacking America Under the Threat
of Bankruptcy. Appleton, WI: John Birch Society.
National Review Editors. 2001. �The 9/11 Toll.� National Review. December17.
Odell, John S. 1996. �Explaining Change in Foreign Economic Policy.� American
Foreign Policy: Theoretical Essays, Ikenberry, John G. Ed. New York: Harper
Collins College Publishers.
Paterson, Thomas G. 1984. Major Problems in American Foreign Policy. Lexington,
MA: DC Heath & Company.
School of Americas Watch. 2002. www.soaw.org. Retrieved March 18.
Sheehan, Neil et al. 1971. The Pentagon Papers. Toronto: Bantam Books.
Stern, Jessica. 1999. The Ultimate Terrorists. Cambridge: Harvard Univ. Press.
Spanier, John, and Steven W. Hook.1998. American Foreign Policy Since World War
II. Washington, DC: CQ Press.
Truman, Harry S. 1995. Memoirs by Harry S. Truman. 1945: Year of Decision. New
York: Smithmark Publishers.
22.U.S.C. 2656 f(d).
Wekesser, Carol. Ed. 1993. American Foreign Policy: Opposing Viewpoints. San Diego:
Greenhaven Press.
Whittaker, David J. Ed. 2001. The Terrorism Reader. London: Routledge.
Zinn, Howard. 1995. A People�s History of the United States: 1492 � Present. New York: Harper Perennial.
©